The Windows registry
is one of the main administrative tools on Windows OS. It is a
hierarchical database that stores configuration settings and options on
Microsoft Windows operating systems. When the system is infected virus,
the virus file first disables the windows registry to prevent further
editing. Even if the virus is removed the registry still remains as
disabled. Then a dialogue box will appear when the user tries to open ‘regedit’, showing “Registry Editing has Been disabled by your administrator”. Now we are discussing two simple tips to overcome this trouble.
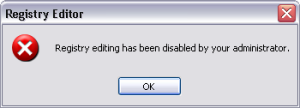
Regedit Dialogue Box
1.
Use the Group policy editor
Run GPEDIT.MSC
%windir%\system32\gpedit.msc
On GPEDIT configure the settings like this.
User Config\Admin Templates\System\Prevent Access To registry Editing Tools=
“Not Configured”
You can set the value to “Not Configured” or “Disabled”.
2.
Rename Regedit.com to Regedit.exe
Some viruses and
other malware will load a regedit.com file that is many times a zero
byte dummy file. Because .com files have preference over .exe files when
executed if you type REGEDIT in the run line, it will run the
regedit.com instead of the real regedit.exe file.
Delete the regedit.com file if it’s a zero byte file to restore access to REGEDIT. In some cases, such as the W32.Navidad worm, you’ll need to rename the REGEDIT file to get it to work.
